what
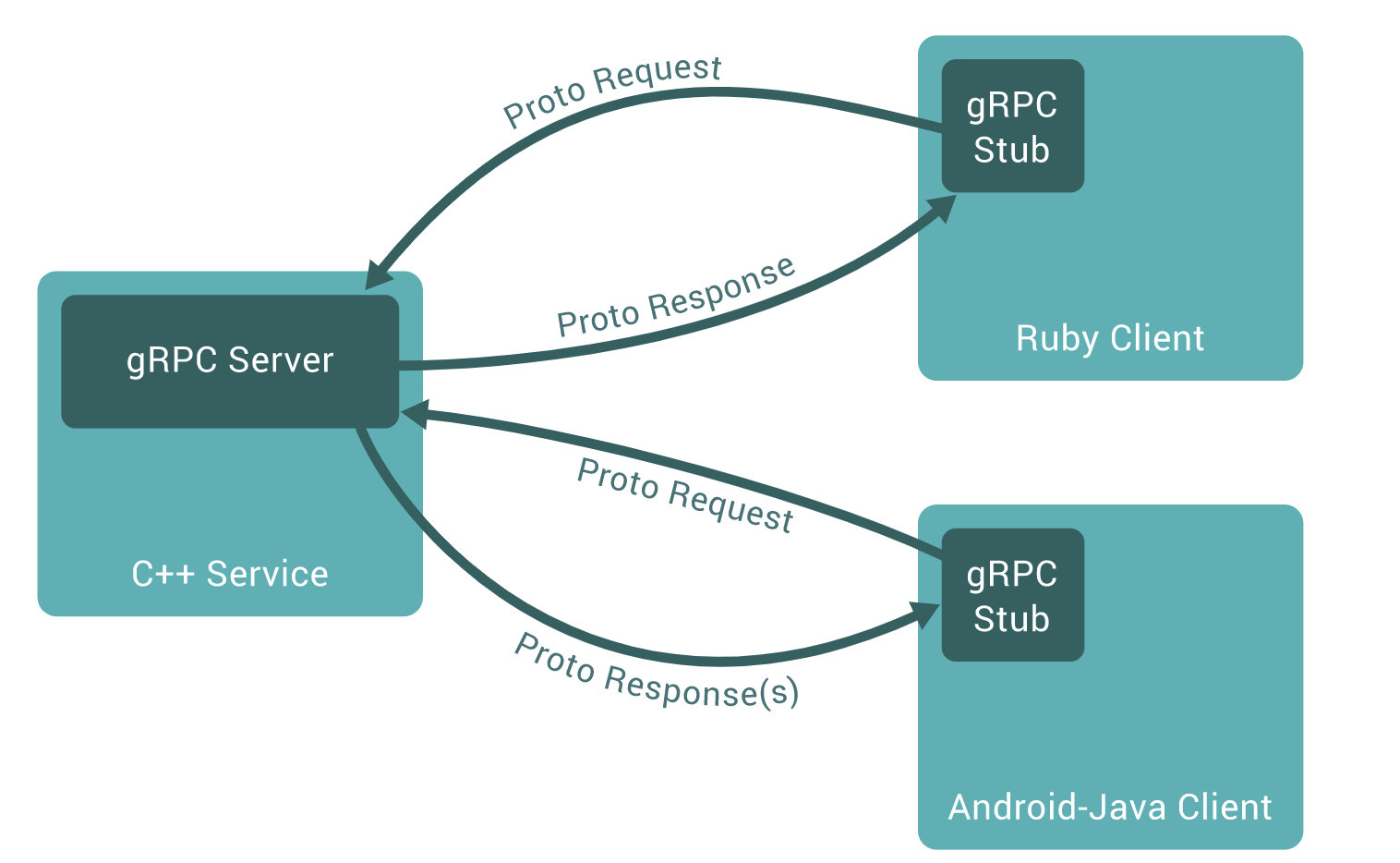
gprc 是一种通信协议 ,使用protocol buffers作为结构数据序列化机制,通信协议格式
分成client server
- client
就像本地对象一样,可以远程调用不同机器server上的方法,轻松地创建分布式应用程序和服务
- server
服务器实现此接口并运行gRPC服务器来处理客户端调用
install
1 | |
how
- 定义
*.proto消息结构体,服务 protoc --go_out=plugins=grpc:. *.proto生成对应语言的协议接口 ( client server接口 && 消息的请求响应序列化 )通过 protocol buffer 的编译器 protoc 以及一个特殊的 gRPC Go 插件来完成
ssl
server
1 | |
1 | |
metadata header 过滤器
grpc获取nginx header的value,使用metadata从context获取
1 | |
1 | |
拦截器
1 | |